Home » Blog » IP Security
What Is a Firewall? A Guide to Cybersecurity
Learn all about firewalls, how they function, how they are configured and what different types of firewalls exist with this comprehensive guide.

In short, a firewall is a network security device that helps protect users’ networks by filtering traffic and blocking malicious content. This type of security technology is an essential element in cybersecurity that helps mitigate the growing risk of cyberattacks. But what is a firewall exactly, and how does the firewall security work?
We dive deep into the topic and discuss how a firewall works and how to configure it to ensure efficient security. Continue reading to learn more.
How does a firewall function?
Firewalls can detect threats by monitoring incoming and outgoing traffic. They guard a computer’s entry point to make sure only trusted data packets can enter the network. If a firewall finds potentially malicious packets, it prevents them from entering a user’s private network and personal computers or other devices.
More specifically, a set of security rules in traditional firewalls define how data blocks should be treated: allowed or discarded. These rules determine which Internet Protocol addresses (IP addresses or IPs) and ports are trustworthy.
Unfortunately, some firewalls scan only packet header information, like source addresses, and do not see whether the packet contains malicious code. In comparison, other firewalls perform a deeper examination of the packet content to ensure greater security.
More advanced firewalls can help prevent malware, like viruses, spyware and ransomware, from entering your device. This is important because when fraudulent software enters a device, malicious users can take over control and, potentially, steal sensitive data and jeopardize virtual security.
As you may know already, both software firewalls and hardware firewalls exist. For example, a router is a physical firewall, and a program installed on a device is a software firewall. Software firewalls are also known as host based firewalls because they run on devices connected to a network. A virtual firewall, on the other hand, is software that secures cloud environments.
How are firewalls configured?
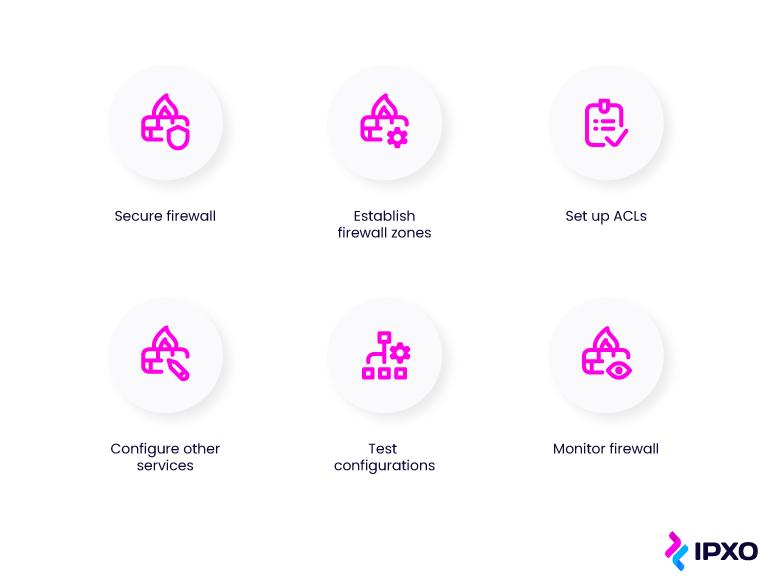
It is important to properly configure firewalls to ensure efficient protection against cyberattacks. There are a few steps to complete while configuring your firewall:
- Secure your firewall
- Establish firewall zones and configure IP addresses
- Set up access control lists
- Configure other firewall services
- Test your configurations
- Monitor your firewall
Secure your firewall
It is important to regularly update your firewall to the latest firmware to ensure maximum protection. Due to outdated settings, your devices and network may be more vulnerable to malicious acts.
Also, consider how many administrators will be managing the firewall. They should have separate accounts and access rights depending on their responsibilities.
Finally, do not forget to change default passwords and update weak combinations to complex ones, as this can significantly increase the level of security overall.
Establish firewall zones and configure IP addresses
You must identify your network’s assets to establish the best protection. This means that you need to group your assets into zones – a portion of the network with specific security requirements – depending on the function and data sensitivity.
For example, you may organize your web-based services, like email servers and virtual private network (VPN) services, into a dedicated zone. That zone can limit the incoming internet traffic to add an extra layer of security to the network.
A good rule of thumb is that the more zones you create, the more secure your network is. Of course, the more zones you have, the more management work your network administrators must perform; therefore, create a system that makes zone administration easier.
Also, when you create your zones, you should make sure that you use internal Internet Protocol addresses for all internal network communication. Additionally, configure network address translation (NAT) to allow internal devices to communicate on the internet.
Set up access control lists (ACLs)
Once you establish network zones, you need to create firewall rules, or access control lists (ACL). ACLs allow or deny traffic depending on the source, destination and port.
In simple terms, ACLs filter the incoming blocks of information by comparing them to specific rules. If they match the configured rules, the firewall can forward the packets to their destination.
Configure other firewall services
You can configure some firewalls to support the Dynamic Host Configuration Protocol (DHCP) or Network Time Protocol (NTP) server functions and other services. If you are not going to use additional services, you can disable them to allow your firewall to work more efficiently.
Test your configurations
Once you make all configurations, it is crucial to test them and ensure that the firewall blocks the intended traffic according to your settings. You can verify proper functioning using different techniques; for example, vulnerability scanning and penetration testing.
Note: Do not forget to back up your configurations in case any hardware failures occur during testing. Otherwise, you might lose your hard work and need to set up all the information again.
Monitor your firewall
Proper management and monitoring of your firewall are critical to ensure that it works as intended. You should regularly monitor firewall logs, update firmware and review rules to make sure that your network is protected efficiently.
Types of firewalls
There are quite a few firewall examples that offer different functionalities:
- Packet filtering firewalls
- Stateful inspection firewalls
- Proxy firewalls
- Network Address Translation firewalls
- Next generation firewalls (NGFW)
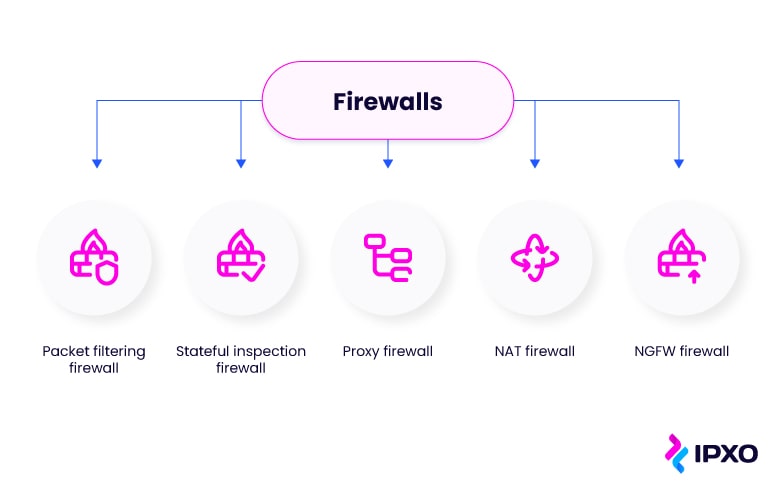
All of these firewalls provide a different level of security depending on your needs. Perhaps you are looking for a firewall for your business? Continue reading to learn more about each type and how they work to choose the most suitable option.
Packet filtering firewalls
Packet filtering firewalls offer basic network protection. They operate at the network layer of the Open Systems Interconnection (OSI) model, which means they make decisions based on network addresses or port information.
In other words, this firewall technology works by filtering individual data packets according to user-defined IP addresses. This means that if this type of firewall detects a data packet from an undefined IP address, it does not forward the packet to its destination.
Packet filters work quickly and efficiently because they do not perform an extensive analysis of the data block content. Also, a packet filtering firewall can offer user-friendly and efficient protection without considerable investments in expensive software. That is because one router can protect the entire network.
However, packet filtering firewalls have limitations. For example, they allow all web traffic which means that they may not prevent all web-based attacks. Moreover, packet filter firewalls cannot protect against malicious content from a trusted IP address because they do not perform a deeper analysis of the incoming information.
Also, these firewalls do not protect against IP spoofing. Therefore, in theory, hackers can employ fake IPs to bypass the firewall and gain access to the network.
Stateful inspection firewalls
Stateful inspection firewalls, or dynamic packet filtering firewalls, verify an established network connection and can determine if the traffic or sent content is malicious. Unlike packet filtering firewalls, they perform deeper checks of the packet content, not only header information, IP addresses or ports.
A stateful multilayer inspection firewall (SMLI) is the more advanced version of a packet filtering firewall. SMLI examines major OSI model layers: network, transmission and application layers. To put it simply, SMLI analyzes packets on these three levels and compares them to already known packets. This comprehensive analysis ensures safer communication between networks.
On the flip side, a stateful inspection firewall is expensive and might be more complex to configure than packet filtering firewalls. Therefore, network administrators might need more time or skills to set up the software properly.
From a security standpoint, a stateful inspection firewall is vulnerable to man-in-the-middle or denial-of-service (DoS) attacks; therefore, it should be used in combination with other software to ensure more efficient protection.
Proxy firewalls
A proxy firewall, or application firewall, is a security system that filters messages at the application layer. A proxy firewall performs a deep packet inspection to analyze the packet’s content against the security rules. If packets comply with these rules, they are forwarded to their destination.
To put it simply, when information comes in, proxy servers filter traffic and discard malicious data. In a proxy firewall, a proxy server acts as an intermediary between the device and the internet, thereby protecting both users and their hardware.
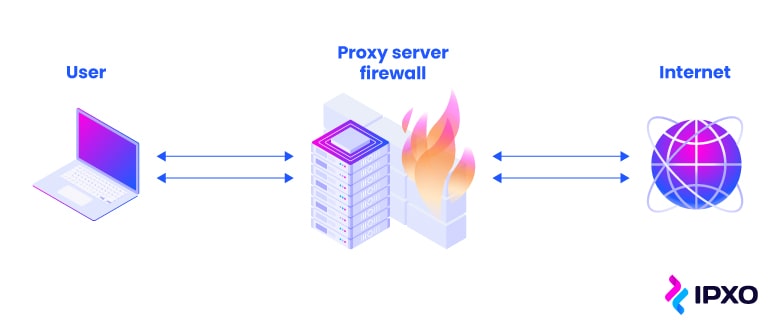
For example, when a user requests a web page, a proxy server sends this message to the web server and hides the user’s geolocation protecting them from potential attacks.
Unfortunately, proxy firewalls have their downsides. For one, they create a new connection for each individual packet, which may slow down the performance of the network. Moreover, a proxy firewall may require more complex configurations than stateful configuration firewalls.
Also, some proxy firewalls are not compatible with all network protocols limiting the applications that can be secured.
Network Address Translation firewalls
One more network-based firewall is the Network Address Translation (NAT) firewall, which works on a router to protect private networks.
To put it simply, the NAT firewall does not show your device’s private IP address to the wider net. Instead, NAT translates an internal IP address to a public IP address that allows devices to communicate with the internet.
Furthermore, the NAT firewall allows incoming traffic if a device on a private network requests it. In other words, outsiders cannot connect to your computer unless your device requests it. This helps avoid communication with potentially harmful devices on the internet.
However, NAT firewalls do not have other security features like other modern firewalls do. For example, the deep packet investigation or intrusion prevention systems (IPS). This means that NAT firewalls may be vulnerable to more sophisticated attacks, like phishing.
Therefore, if you rely only on NAT to protect your network traffic and your sensitive data, you should employ other security measures, like anti-virus security software, to ensure more robust security.
Next generation firewalls
A next generation firewall (NGFW) is a network firewall that combines several standard firewall capabilities. These can include packet filtering, stateful inspection and deep packet inspection. This means that next generation firewalls inspect the origin of the message and its content, so they can efficiently block malicious data.
Also, NGFW monitors incoming traffic and outgoing network traffic to prevent potentially dangerous traffic based on security rules. Next generation firewalls do this by inspecting layer 7 – the application layer – of the OSI model and preventing malicious applications from entering a network.
A next generation firewall can also have intrusion prevention systems integrated that help protect against more sophisticated cyberattacks.
To further increase security, these firewalls can also be a part of the unified threat management (UTM) system. NGFW is sometimes referred to as UTM because they both have similar capabilities and complement one another in network security.
Despite that next generation firewalls guarantee the security of your network, they may cost more than packet filtering or proxy firewalls. Also, users might need to add additional configurations to the existing network security systems, which may complicate the integration of the firewall.
Conclusion
Undoubtedly, all network-based firewalls perform a crucial function in protecting a user’s internal network from outside threats. However, one firewall might not be enough to ensure robust protection against different cyberattacks. Especially, if you are running a business that processes a lot of sensitive data and requires a comprehensive security solution.
When choosing a firewall for your business, it is important to consider several factors. First, take into account the size of your company. If you own a small business, one firewall for an entire network might suffice. On the other hand, if you operate a large infrastructure, one network firewall might not secure it.
Also, suppose you process a lot of sensitive data that might be at risk in the event of a cyberattack. In that case, you should employ several traditional firewalls or use more sophisticated technology, like a next generation firewall.
Luckily, a combination of network firewalls with different security features can ensure more robust protection of your network traffic. For example, a combination of packet filtering and proxy firewalls may help spot potential threats on time and, in turn, prevent them from attacking your devices.
If you have any virtual environments on-site, you can employ software/virtual firewall capable of protecting your virtual networks.
If you end up investing in several network firewalls, do not forget to properly configure them to ensure the best possible protection. Also, always keep the firewalls up to date to improve their performance and fix bugs or patch vulnerabilities.
Ultimately, investing in a high-end firewall or a combination of them is worth the money because you can protect your business network and your data from advanced cyberattacks. When you implement appropriate measures, you can share data across the internet without putting your entire company’s infrastructure at risk.
About the author
Table of contents
How does a firewall function?
How are firewalls configured?
Secure your firewall
Establish firewall zones and configure IP addresses
Set up access control lists (ACLs)
Configure other firewall services
Test your configurations
Monitor your firewall
Types of firewalls
Packet filtering firewalls
Stateful inspection firewalls
Proxy firewalls
Network Address Translation firewalls
Next generation firewalls
Conclusion
Related reading

The Do’s and Don’ts of IP Address Abuse Observability
As the IPXO Abuse Prevention team continues to improve services and ensure high abuse observability at the Marketplace, let's take a look at the do's and don'ts that every…
Read more
Infographic: IPXO 2022 Q3 Abuse Prevention Statistics
Your comprehensive view of the IP address abuse handling at the IPXO Marketplace during the third quarter of 2022.
Read more
Infographic: IPXO Q2 2022 Abuse Prevention Statistics
A comprehensive view of the most common threats IPXO Abuse Prevention experts faced during the second quarter of 2022.
Read moreSubscribe to the IPXO email and don’t miss any news!
