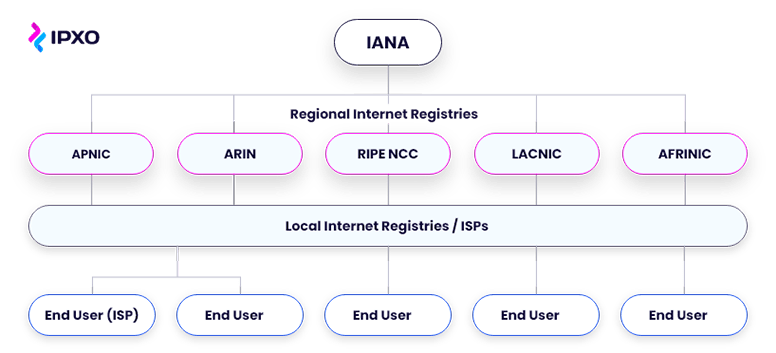
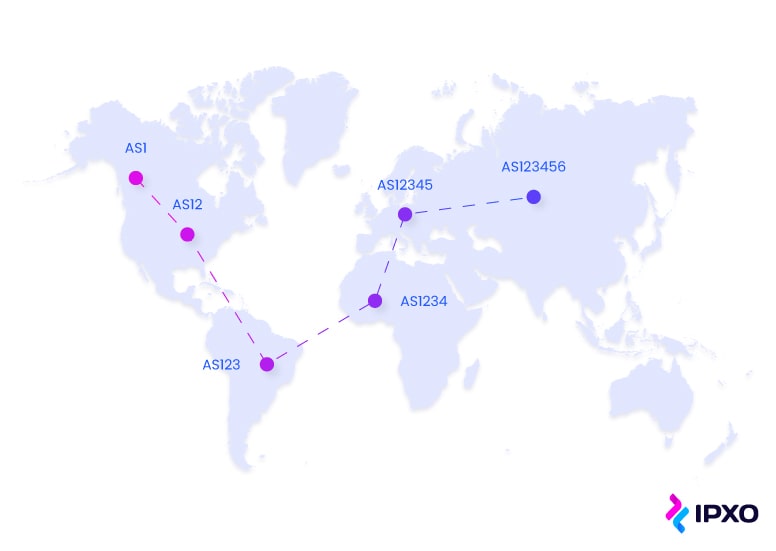
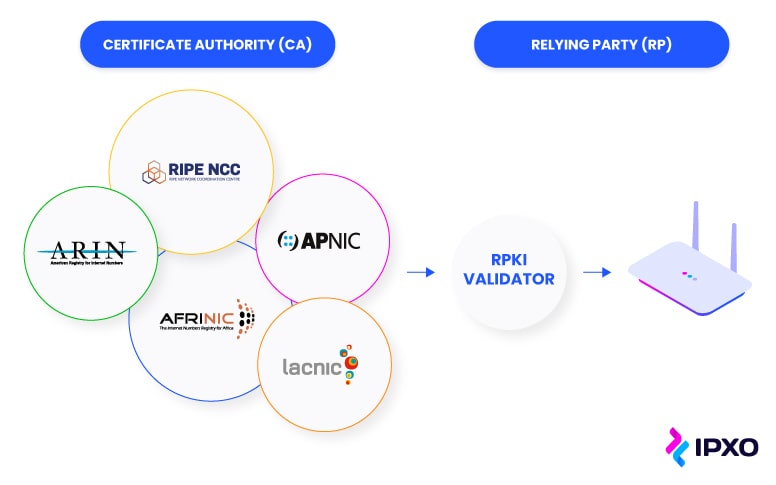
What Is RPKI? Resource Public Key Infrastructure For Beginners
6 min read
18 November 2021
Ignas Anfalovas
Here's all you need to know about the Resource Public Key Infrastructure, how it works and how to use it.

About the author
Ignas is a Platform Engineering Manager at IPXO with more than 7 years of experience in the IT sector. His expertise includes network design solutions and infrastructure maintenance. After working hours, you will find Ignas in Lithuanian folk-dance classes.
Table of contents
Related reading

7 December 2022 •
IP Reputation,
IP Security
The Do’s and Don’ts of IP Address Abuse Observability
As the IPXO Abuse Prevention team continues to improve services and ensure high abuse observability at the Marketplace, let's take a look at the do's and don'ts that every…
Read more
25 October 2022 •
IP Security,
Original Insights
Infographic: IPXO 2022 Q3 Abuse Prevention Statistics
Your comprehensive view of the IP address abuse handling at the IPXO Marketplace during the third quarter of 2022.
Read more
6 September 2022 •
IP Security,
Original Insights
Infographic: IPXO Q2 2022 Abuse Prevention Statistics
A comprehensive view of the most common threats IPXO Abuse Prevention experts faced during the second quarter of 2022.
Read moreSubscribe to the IPXO email and don’t miss any news!