What Is a Subnet Mask? 2024 Updated Guide
What's the difference between a subnet and a subnet mask? What is subnetting and how can it help you? Discover answers to these and many other questions in this article.
A subnet mask is a number that distinguishes the network address and the host address within an IP address. A subnet is a smaller network within a network that requires a subnet mask.
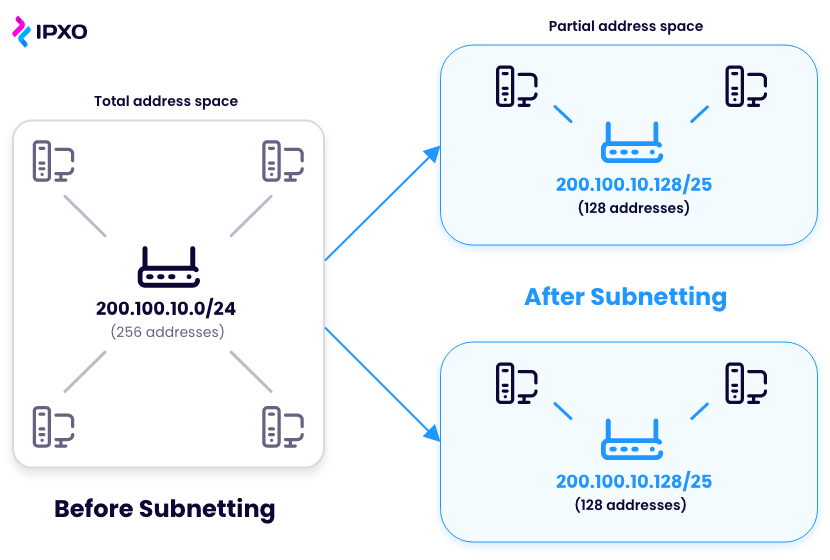
Subnetting is the process of dividing a network into two or more subnets. Its primary function is to make the routing of data within a network more efficient and secure. Subnetting also helps make better use of IPv4 addresses.
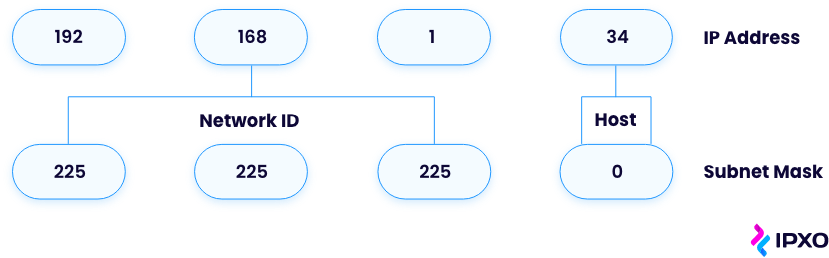
When you connect a device to a network, the network assigns an IP address to the device. That IP address consists of two parts: the network portion and the host portion. The network portion of the IP address identifies the overall network while the host portion identifies the device.
The network address and host address contained in an IP address are indistinguishable from each other without a subnet mask. The subnet mask allows network traffic to understand IP addresses by splitting them into the network and host addresses.
You can quickly see which subnet mask would apply to which subnet and IP address pairing using a subnet cheat sheet.
Are subnets and subnet masks the same thing?
No, while subnet masks are an essential part of subnets, they are not the same thing.
A subnet (short of subnetwork) describes the specific part of a network that shares the network’s IP address but has a unique subnet address.
A subnet mask, however, differentiates between the portion of an IP address that refers to the subnet and the portion which refers to the host.
Why use subnetting?
Implementing subnets and subnet masks empowers organizations to enhance security, streamline network operations, and optimize performance to meet their business needs effectively.
Here are some of the key benefits.
More efficient routing of data
Broadcast traffic creates a big inefficiency in networks. This traffic involves data packets traversing the network to every node. By dividing broadcast domains, subnetting reduces the number of nodes that broadcast traffic interacts with and makes the routing of data packets more direct and efficient.
For example, imagine an ISP serving customers across a wide geographical area. By subnetting, the ISP can create smaller networks for users in different regions, resembling breakout rooms in a Zoom call where conversations are more focused.
Subnet masks are key here. That’s because a subnet mask is what makes sure that traffic stays contained within its designated subnet. This reduces major congestion and the load imparted on the network.
Subnetting effectively decreases the distance that data packets need to travel in the network. This also allows the network to route data more efficiently.
All of this increases the speed and overall performance of the network.
Better network security
If you’re operating a large local network, with many connected devices and a high volume of network traffic, there are a number of security advantages of running multiple subnets rather than one larger network.
Most notably, if a subnet is compromised by an attack, only that network segment will be affected. Using subnets, instead of all devices on the same network being visible to attackers, they would only have access to other devices on the same subnet.
Consider a scenario where a company segregates its internal network into different subnets for departments like HR, Finance, and Operations. If one subnet is compromised, attackers would only gain access to devices within that department, minimizing the overall impact.
A network manager who breaks a local area network into smaller networks can also control the flow of traffic through Route-maps, QoS, or ACLs, which helps identify and address threats more effectively.
You may want to create subnets to keep legitimate local network traffic siloed, too. Subnets make it possible to prevent all devices from accessing the entire network. This is a great solution if you want to keep certain files or processes secure or limit remote network access.
Increased lifespan of IPv4
When the internet was first coming into use, it was easy to get an IP address. Since there is a limited number of possible IPv4 addresses, the available IP address stock quickly began to diminish.
Looking for an IP address solution, creative minds came up with the idea of using subnetting to increase the utility of a single public IP address.
Rather than assigning a unique IP address to each device, subnetting allows multiple private IP addresses to exist within a single IP network. This means that each device on an IP network has an IP address with a part that refers to the overall network IP address, and a part that refers to its subnet.
This approach significantly extends the viability of IPv4 as the internet standard, demonstrating how subnetting plays a crucial role sustaining the longevity of IPv4.
IPXO and subnetting
At IPXO, we provide clients with the possibility to divide large ranges into smaller subnets, specifically serving businesses that prioritize smaller network segments.
This level of flexibility empowers companies to customize their network infrastructure to suit their specific needs, ultimately improving operational efficiency and performance.
Moreover, with Bring Your Own IP (BYOIP) feature, you can bring a larger subnet leased from IPXO into AWS, Google Cloud, Microsoft Azure, or any other cloud infrastructure that supports BYOIP. Then, you can easily segment it into smaller ranges within your account.
How does subnetting really work?
Networks use Internet Protocol addresses to identify specific pieces of hardware, like servers or computers. Subnetting allows a network with one public IP address to split into smaller networks. Each with a unique internal IP address.
Networks are capable of connecting hundreds and even thousands of devices. As a result, traffic may have to travel a complex route to the associated IP address for a specific device.
Subnetting creates sub-networks within a single physical network, limiting IP address usage to just a few devices. Due to this, data can travel more directly to its destination IP address. It doesn’t need to interact with all parts of the network.
To identify the specific device that a data packet is going to, it is important to arrange the IP address in a logical way. The purpose is to ensure that it is easy to identify the network address and the host address.
To make subnetting possible, and to make sure traffic gets to the correct destination address, each IP address needs to be matched to a subnet mask.
How do IP classes and subnet masks relate?
Networks come in different sizes. Some require access for just a few hosts. Others need to offer access to many thousands of hosts.
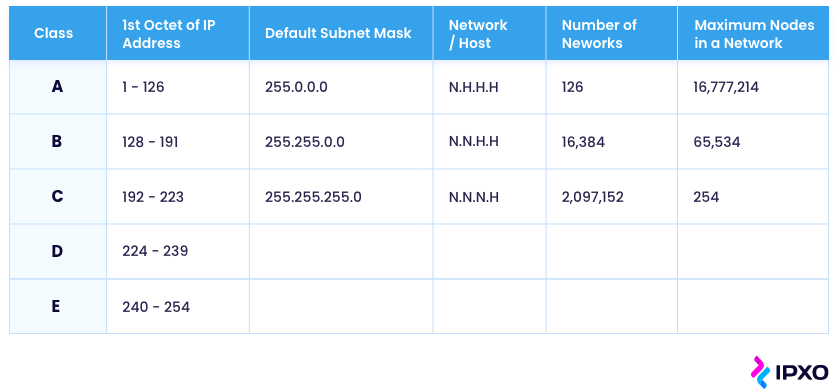
Because of this, there are different classes of IP addresses. They make space for class A networks, class B networks, and class C networks. There are also class D and class E networks. Class D facilitates multicasting and class E – research, so they’re not relevant here.
However, nowadays most IP addresses are classless, but it’s still good to know this system for when you might need it.
The IP address class dictates the possible size of the network as well as how many of the octets are dedicated to the subnet mask. Different IP address classes are suitable for different needs.
Class A network supports over 65,536 hosts. It makes all that access by only having the subnet mask reflect the network address in the first octet, with the second, third, and fourth left free for the administrator to assign as required to hosts and subnets.
Class B network has an IP address where the subnet mask reflects the network address in the first and second octets. Leaving only the third and fourth for assignment with the network. Class B network, therefore, has availability for connections to only between 256 to 65,534 hosts.
Class C network supports the fewest hosts. In a class C network, the first, second, and third octets are all used to reflect the network number. Leaving only the final octet to facilitate up to 254 host addresses.
Both class B address and class C address look the same. Therefore, they require a subnet mask to identify the network address and host address.
How do network addresses and subnet masks relate?
For IPv4 addresses, each of the different classes of the network has a different default mask:
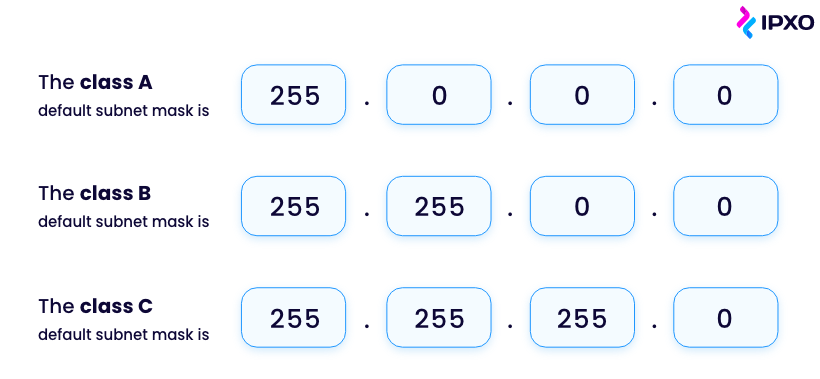
You can see how the default subnet masks reflect how many of the octets are used by the network address.
Looking at the default subnet mask tells you the number and type of IP addresses of any given network. Each subnet contains connected devices with a fixed range of IP addresses.
If you take 10.45.21.0 as an example IP address and pair it with the subnet mask 255.255.255.0, you can determine that the network address is contained in the portion 10.45.21 while the associated subnet for host addresses is in the range 10.45.21.0–10.45.21.255.
Common mistakes in subnetting
Understanding subnetting and subnet masks can be challenging, leading to some common mistakes:
- Inaccurate calculation of subnet sizes. Calculating subnet sizes inaccurately can lead to subnets with insufficient or excessive IP addresses, impacting network scalability and efficiency. Reconfiguration of subnets may cause additional problems on the go.
- Extensive range of subnet. Extensive subnet ranges, covering many devices, expand the broadcast domain within the subnet. This amplifies broadcast traffic, flooding all devices with messages. If the subnet contains numerous devices, this flood can overwhelm the network, causing congestion and potentially triggering a broadcast storm.
- Scattered subnets. Lacking cohesive structure in subnets poses challenges for network management, including tracking IP addresses, uneven resource allocation, and security vulnerabilities. To overcome these issues, organizations should adopt a structured subnetting approach, organizing subnets logically, documenting them thoroughly, and aligning them with network needs. If the organization uses excel for this purpose, there is always room for human error. However, IPXO offers a great management tool – the Next-Gen IPAM – that helps businesses avoid these mistakes.
- Lack of regular maintenance. It’s essential to periodically assess and adjust subnet configurations to accommodate changing network requirements and growth. Otherwise, outdated or inefficient subnet designs may occur.
Current trends
Understanding subnetting and subnet masks is crucial in networking. Especially with the ongoing transition to IPv6 adoption. Best practices now involve combining IPv6 subnetting with IPv4 to handle more devices.
Additionally, new networking technologies like Software-Defined Networking (SDN) and Network Function Virtualization (NFV) have changed how subnets are designed and used.
Conclusion
Understanding what a subnet mask is may be impossible until you begin to understand how IP addresses work and why networks use subnetting. That’s why the answer to what a subnet mask is isn’t completely straightforward.
With this said, you should now have basic knowledge of how IPv4 addresses communicate data between and within networks. The administrators of those networks may choose to use subnetting out of concern for security, routing efficiency, network speed or to preserve more public IPv4 addresses. Usually, it’s a combination of multiple reasons.
If you choose to utilize subnetting in your network, you’ll need to use subnet masks to ensure that inbound traffic is routed to and from the correct host devices. Even if you run a relatively small system, subnet masks can play an integral part in its reliable and smooth operation.
FAQ
- What is a subnet mask?
A subnet mask is a number that distinguishes the network address and the host address within an IP address. - How to find subnet mask from IP address?
To find a subnet mask from an IP address, a subnet mask must be provided. It can be expressed in a standard way (255.255.255.0) or in CIDR notation (f.e. /24). - What is the purpose of a subnet mask?
The primary purpose of a subnet mask is to partition a network into subnets for improved efficiency, security, and management of network resources. - How to do subnetting?
To perform subnetting, you need to determine the number of subnets and hosts required, choose an appropriate subnet mask, and allocate IP addresses accordingly.
About the author
Table of contents
Are subnets and subnet masks the same thing?
Why use subnetting?
More efficient routing of data
Better network security
Increased lifespan of IPv4
IPXO and subnetting
How does subnetting really work?
How do IP classes and subnet masks relate?
How do network addresses and subnet masks relate?
Common mistakes in subnetting
Current trends
Conclusion
FAQ
Related reading

DNS and rDNS: the Hidden Heroes That Keep the Internet Running
Discover the web's overlooked helpers - DNS & rDNS. Learn their importance, benefits, and automation's role in powering the online world.
Read more
Email Service Provider: What You Should Know About ESPs in 2022
Discover the differences between email service providers and webmail clients. Learn the importance of ESPs for successful email marketing campaigns.
Read more
File Transfer Protocol Explained
What does FTP stand for? What is the importance of this protocol? How does it work? Read this post to learn all about the File Transfer Protocol.
Read moreSubscribe to the IPXO email and don’t miss any news!
