What Is Address Resolution Protocol? A Beginner’s Guide to ARP – 2024 Updated
There are different types of Address Resolution Protocol. This article defines them, explains why ARP is important and how it works, and unravels ARP security threats.

The Address Resolution Protocol (ARP) is a communication protocol that maps the Internet Protocol (IP) address to the Media Access Control (MAC) address. This protocol facilitates the communication of the devices connected to the network.
Applications and software connected to the internet use IP addresses to send information. Meanwhile, the communication between systems happens through hardware addresses, also known as MAC or physical addresses. Without ARP, software and devices would not be able to send data to each other.
Continue reading the article to understand how ARP enables communication between devices on the network and why it is important.
Why is ARP important?
ARP translates the software address (IP address) to the physical address (MAC address) of the host connected to the network. ARP exists as the link layer protocol in the Open System Interconnection (OSI) model.
The conceptual OSI model defines the standard of communication between different computer systems. This model uses layers to visualize how various systems employ standard protocols in their communication with each other.
In the OSI model, MAC addresses are a sublayer within the data link layer (therefore, known as data link addresses). The data link layer is responsible for maintaining the connection between two physically connected devices and allows them to transfer data. Meanwhile, IP addresses belong to the network layer. The network layer forwards packets through different routers.
However, destination decisions can’t be based on IP addresses. On the same network, an IP address maps the data link layer address of another computer.
Here’s where ARP comes into play. Since IP version 4 (IPv4) addresses have different lengths (32-bit) than MAC addresses (48-bit), ARP translates these addresses to facilitate the information exchange.
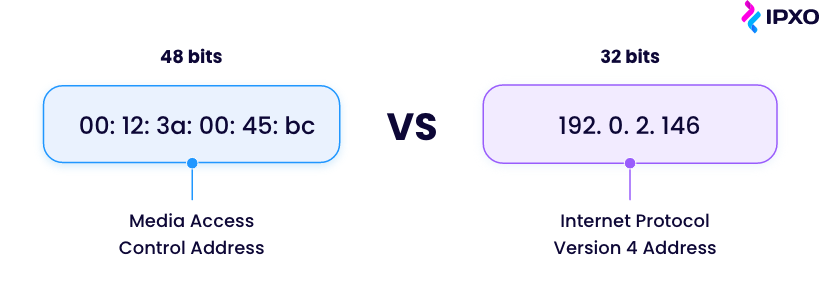
Essentially, without ARP, a host would not be able to figure out the hardware address of another host.
ARP evolution
ARP has evolved over the years to meet the changing needs of modern networks.
It now incorporates ARP spoofing detection tools and dynamic ARP inspection (DAI) to prevent unauthorized manipulation of ARP tables and prevent man-in-the-middle attacks.
Efficiency improvements have been made to assist larger and more complex networks, with IPv6 introducing Neighbor Discovery Protocol (NDP) to facilitate network management.
ARP has adapted to support virtualized environments by ensuring seamless communication between virtual machines (VMs) and host systems. It has also integrated with emerging technologies like cloud computing.
In cloud computing environments, ARP remains essential for facilitating communication between virtual machines (VMs) and other networked resources. Cloud technologies bring dynamic resource provisioning and scaling, necessitating ARP’s adaptation to VM mobility and changing network configurations.
However, ARP security faces risks such as VM escape attacks and ARP spoofing due to the shared nature of resources and multi-tenancy.
How does ARP work?
When a source device wants to send an IPv4 packet to another device, ARP performs two important tasks.
First, the ARP program checks the ARP cache table, which consists of IPv4 address to MAC address mappings.
The second task starts if the ARP cache lookup doesn’t provide a matching MAC address. In this case, the source server forms an ARP message, which is broadcasted on the local area network (LAN).
Let’s discuss how ARP requests work in detail.
ARP request
An ARP request establishes communication between devices on the network. It is enabled after a source device fails to retrieve necessary data from an ARP cache table.
The ARP table holds records of the IP address and MAC address of the devices connected to the same network. IT administrators do not maintain this table. Instead, the ARP protocol creates additions when it receives an ARP response. All operating systems in a network keep ARP caches.
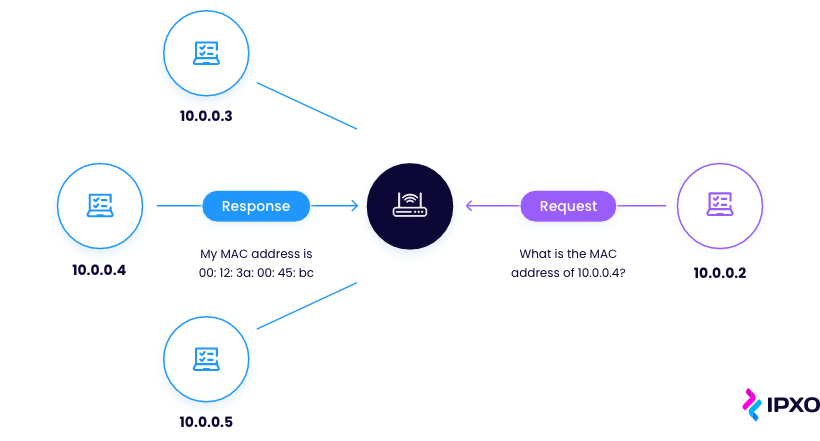
It’s worth noting that the ARP cache size is small. That’s why the cache periodically cleanses itself to free space for new entries.
Here’s a detailed example of the ARP process.
Let’s say there are two computers in a local area network psychically connected by Ethernet cables and network switches, without gateways or routers that intervene. One of the computers, let’s call it Host 1, receives a command to send a packet to the other computer – Host 2.
To reach the destination, Host 1 uses DNS to determine the unique IP address of Host 2. However, it also needs a hardware address to send the packet.
First of all, Host 1 has to check a cached ARP table to look up the IP address for any existing records of the target’s MAC address. If the cached records exist, then Host 1 sends the IP packet through an Ethernet frame (a destination MAC address delivers this frame).
If the hardware address was not available in the cache, Host 1 then sends the ARP request message searching for MAC address of a specific IP. Host 2, which uses the IP address asked by Host 1, reacts by sending an ARP response containing the requested MAC address.
After receiving the ARP response, Host 1 updates its ARP table with the new information and delivers the IP packets.
In Wi-Fi networks, ARP functions similarly to wired networks but operates over the wireless medium, facilitating communication between devices by resolving IP addresses to MAC addresses.
However, wireless environments are vulnerable to ARP-related issues such as spoofing, interference, the hidden node problem, and cache poisoning. We will discuss these issues later in the article.
Types of ARP
There are four types of Address Resolution Protocol:

Let’s take a closer look at each of them.
Proxy ARP
A Proxy ARP protocol handles requests coming from IP addresses that aren’t on the local area network. When the request packet comes from a system outside the host’s network, the Proxy ARP-enabled router responds to the ARP request packet.
However, instead of providing a MAC address of the target host, the router responds by pretending to be the destination and delivers its own MAC address instead. When the source device sends the packets to the destination, they are in fact sent to the destination router which forwards the packets to the actual destination device (within the local network).
Gratuitous ARP
A Gratuitous ARP works as an ARP response that is not evoked by an ARP request. It assists when a host needs to announce or update its IP address to MAC address mapping to the entire network.
Reverse ARP
A Reverse Address Resolution Protocol (RARP) requests IPv4 addresses from the ARP gateway router table. New systems or machines that don’t have the memory to store their own IP addresses tend to use this type of ARP.
The requesting device broadcasts a Reverse ARP packet with its own MAC address in the address field of both the sender and the receiver hardware. The RARP server installed in the local network responds to the request. The server then locates a mapping table entry in the IP to MAC address. If the matching is successful, the server sends the response packet with the IP address of the requesting computer.
Inverse ARP
An Inverse ARP (InARP) does the opposite of what a traditional ARP does – it maps IP addresses using the associated hardware addresses. InARP assists when a device knows the Data Link Connection Identifier (DLCI) of a remote router but does not know its own IP address.
Possible security threats
ARP spoofing
Also known as ARP cache poisoning or ARP poison routing, ARP spoofing is a malicious cyberattack carried out by cybercriminals, sending out fake ARP messages to a target LAN.
This allows the attacker to link their MAC address with the IP address of a device on the network. If the ARP poisoning attack is successful, the criminal’s computer receives data from the victim’s computer.
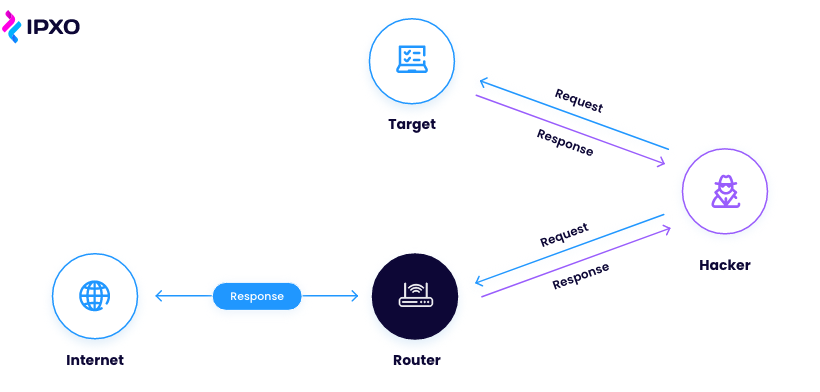
Needless to say, these data breaches can cause serious harm and are acted out without the computer’s owner even noticing.
You can avoid ARP spoofing, by using ARP spoofing detection tools, implementing static ARP entries, enabling dynamic ARP inspection (DAI), employing port security on switches (e.g. MAC address limiting), implementing VLAN segmentation, and encrypting network traffic.
Denial-of-Service (DoS) attacks
Attackers often use a denial-of-service attack to overwhelm servers, computer networks and systems by flooding them with traffic. A large-scale DoS attack is known as a distributed denial-of-service (DDoS) attack. DDoS uses a much greater number of resources to flood the system and prevent users from accessing it.

When a large number of ARP packets are transmitted through a vulnerable network, the service can become overwhelmed.
Avoid DoS attacks, by deploying firewalls and intrusion detection/prevention systems, using rate limiting and access controls, employing DDoS protection services, and implementing redundancy in network infrastructure.
Man-in-the-Middle (MITM) attacks
Another common attack is called man-in-the-middle. During this attack, a third party – a cyberattacker – finds a way to intercept between two other parties and steal information.
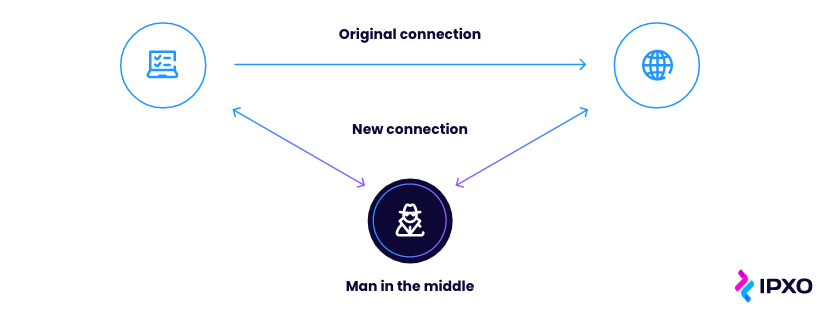
Use encryption protocols for secure communication to avoid MITM attacks. Deploy digital certificates and SSL/TLS, use MFA methods for authentication, monitor network traffic for anomalies, verify the integrity of network devices, and avoid unsecured public Wi-Fi networks, or use VPN when using public networks.
Session hijacking
ARP poisoning can also lead to session hijacking attacks. They occur when a cybercriminal takes over the user’s web session after stealing their session ID. If the attack is successful, cybercriminals can mimic the user’s identity and perform actions on their behalf.
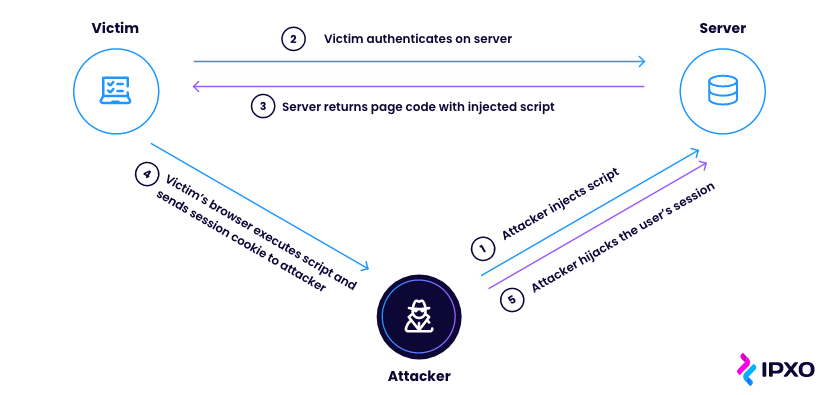
Don’t forget to use HTTPS for secure communication, enforce strong session management practices (e.g. implementing session expiration timeouts), employ encryption for sensitive data transmission, and implement multi-factor authentication to avoid session hijacking.
Conclusion
The Address Resolution Protocol (ARP) is an important protocol that can map IP addresses to MAC addresses. It facilitates communication between devices on the same network. Without ARP, software and devices would not be able to send data to each other.
ARP has several important types: Proxy ARP, Gratuitous ARP, Reverse ARP and Inverse ARP. All these types serve as communication protocols on the local area network.
Unfortunately, the ARP protocol is vulnerable to spoofing, DoS and Man-in-the-Middle attacks, and session hijackings – malicious cyberattacks performed by cybercriminals. Security measures should be taken to ensure ARP security.
FAQ
- What is Address Resolution Protocol (ARP)?
Address Resolution Protocol is a communication protocol used to map IP addresses to MAC addresses on a local network. - Why is ARP necessary for communication in networks?
ARP is necessary for communication in networks because it resolves IP addresses to MAC addresses, allowing devices to properly address and communicate with each other on the same local network segment. - What are the 4 main types of ARP?
Proxy, Gratuitous, Reverse and Inverse ARP. Each of them serves specific functions in resolving IP-to-MAC address mappings and maintaining network connectivity. - What are ARP-related security risks?
Common ARP-related security risks include ARP spoofing, ARP cache poisoning, and the potential for man-in-the-middle attacks. - What measures can be taken to prevent ARP spoofing attacks?
To prevent ARP spoofing attacks, implement ARP spoofing detection tools, enable dynamic ARP inspection (DAI), configure static ARP entries, and deploy network segmentation and encryption techniques.
About the author
Table of contents
Why is ARP important?
ARP evolution
How does ARP work?
ARP request
Types of ARP
Proxy ARP
Gratuitous ARP
Reverse ARP
Inverse ARP
Possible security threats
ARP spoofing
Denial-of-Service (DoS) attacks
Man-in-the-Middle (MITM) attacks
Session hijacking
Conclusion
FAQ
Related reading

IPv4 Packet Header: Format and Structure
When you think about it, the IPv4 packet format is truly fascinating. Learn about the elements at play with this comprehensive guide.
Read more
File Transfer Protocol Explained
What does FTP stand for? What is the importance of this protocol? How does it work? Read this post to learn all about the File Transfer Protocol.
Read more
TCP/IP: What Is It And How Does It Work?
The Transmission Control Protocol and the Internet Protocol create what is known a TCP/IP model. Learn how it works and what functions it serves.
Read moreSubscribe to the IPXO email and don’t miss any news!
