The Do’s and Don’ts of IP Address Abuse Observability
6 min read
7 December 2022
Gustavas Davidavičius
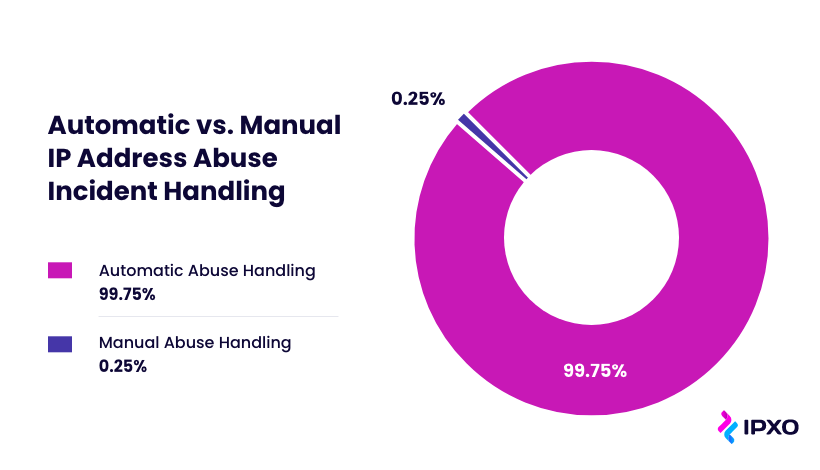
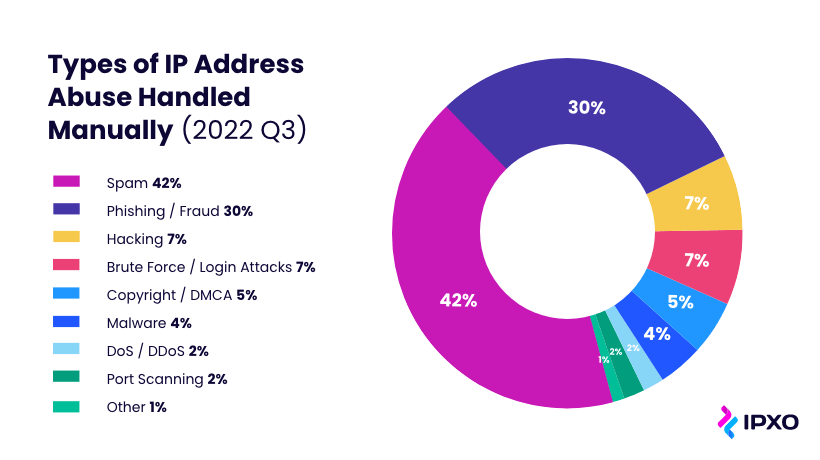
As the IPXO Abuse Prevention team continues to improve services and ensure high abuse observability at the Marketplace, let's take a look at the do's and don'ts that every IP address user should remember.

About the author
Gustavas is a Senior Abuse Prevention Specialist at IPXO. He specializes in the abuse desk policies, as well as IP reputation upkeep on the IPXO’s IP leasing and monetization platform.
Table of contents
Related reading

15 September 2022 •
Internet Protocol,
IP Reputation
IP Warming for Email Campaigns: What Is It and Why Is It Important?
What is IP address warming? How does it work? What kinds of challenges can you face when warming IPs? How can you benefit from this practice? We've got all…
Read more
20 December 2021 •
IP Reputation
How To Remove IP From Barracuda Blocklist? A Comprehensive Guide
The Barracuda blocklist serves an important role, but how does it block IP addresses? And what steps must be taken to remove IPs from BRBL?
Read more
17 December 2021 •
IP Reputation
How To Remove IP From Spamhaus Blocklist: Step by Step Guide 2023
Have you found your IP address in a Spamhaus blocklist? Learn what that means and what steps you should take next.
Read moreSubscribe to the IPXO email and don’t miss any news!