IPXO Webinar: RPKI – Security, Benefits and Adoption
What is RPKI? What problems does it solve, and why is it important? These were the topics discussed in last week’s IPXO webinar. Scroll down to find the full recording.

On June 21, 2022, we invited leading experts to discuss the Resource Public Key Infrastructure (RPKI) in terms of security, benefits and adoption.
Vincentas Grinius, CEO & Co-Founder of IPXO, moderated the discussion. Four esteemed panelists joined in: Nathalie Trenaman – Routing Security Programme Manager at RIPE NCC, John Curran – President and CEO of ARIN, Melchior Aelmans – Chief Architect at Juniper Networks and Ignas Anfalovas – Platform Team Engineering Manager at IPXO.

What is RPKI, and why is RPKI important?
Nathalie Trenaman began the discussion by explaining the basics of the Resource Public Key Infrastructure, including what it is and how it emerged.
Trenaman first gave a three-minute crash course on the Border Gateway Protocol (BGP) and how it helps route data packets on the internet in the most efficient way possible. However, in the early days of BGP – 35 years ago – everyone knew all the networks and their owners, which meant that routing was easy.
Simply put, if any routing issues occurred – for example, typos in routing tables – IP holders could simply call each other and solve the problems individually. Regional Internet Registries (RIRs) even created databases containing contact and routing information. They allowed verifying the rightful owners of IP address blocks.
Although the databases were very helpful in the early days, various problems started occurring as networks expanded and people started forgetting to update routing information. Furthermore, as more databases emerged, it was difficult to track who had the most up-to-date information.
To add insult to the injury, BGP, as Trenaman put it, is not a “forgiving protocol,” meaning it is hard to prevent accidents. Unfortunately, the so-called fat-finger errors (typos) and policy violations (leaks) are common.
Trenaman then referenced a 2020 Routing Security Review to discuss BGP hijack events and route leaks.
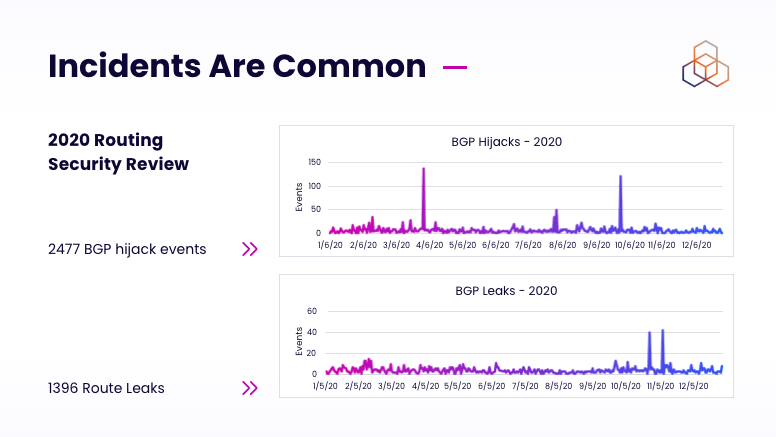
How RPKI emerged
Around 2010, the Internet Engineering Task Force (IETF) started making plans to create trustworthy routing statements that could help make proper routing decisions. This paved the path for the Resource Public Key Infrastructure in 2011.
Trenaman explained that RPKI allows making authorized statements from resource holders. This means IP holders can create digitally signed and verifiable statements about BGP routing intentions. That allows network operators to make more informed and trusted routing decisions.
RIR members and IP holders can generate certificates – cryptographically signed objects – and make routing statements called Route Origin Authorization (ROA) objects. ROAs are collected in RPKI repositories, or databases, and routers can pick up that information. Then, operators can analyze that information and make routing decisions.
How does RPKI solve problems from a network standpoint?
Ignas Anfalovas agreed with Trenaman’s idea that BGP is a very old protocol created when internet security was not a major focus. He also further emphasized that BGP traffic redirections can result in route leaks, route hijacking and IP address spoofing.
Anfalovas gave an example of a BGP hijacking incident that occurred on April 16, 2021. 30,000 prefixes, some of which belonged to Google and Cloudflare, were mistakenly announced, which caused a spike in misdirected traffic. Although this hijacking incident was not intentional, no one found its cause. Interestingly, around 80% of hijacked routes had no ROAs.
Anfalovas concluded that the implementation of RPKI could have significantly minimized the incident and has the potential to minimize the risk of such BGP hijacking incidents in the future.
Melchior Aelmans added that it is great that most incidents are just accidents. However, since BGP connects every network and mistakes propagate quickly, the integration of RPKI is very important. Aelmans shared that Juniper Networks is adamant about educating customers on RPKI and helping implement it.
What is the ideal scale of RPKI adoption?
John Curran reiterated the idea that BGP was not created with security in mind. The aim was to find the most efficient route for the data to send. If any issues with the network occurred, they were quickly solved simply because “everybody knew everyone.” However, as the internet kept growing, validating information became crucial.
From the scale perspective, Curran thinks that we don’t necessarily need a critical mass of organizations that adopt RPKI. According to him, “the main question is do you want to protect your own routing or not.” He concluded that RPKI is an important framework that plays an important role.
What are the key aspects of Hosted, Delegated and Hybrid RPKI?
Curran started answering the question by explaining the important role of RPKI.

Curran then defined the different RPKI services offered by ARIN: Hosted, Fully Delegated and Hybrid RPKI.
- Hosted RPKI is for users who want to publish information about what AS numbers should be announcing their network. ARIN stores and publishes ROAs. In short, users create ROAs, and ARIN publishes them, which is a simple model that a lot of people use successfully.
- Delegated RPKI is for users who run their own RPKI infrastructure using a certificate authority (CA) with a certificate repository of digital certificates, including ROAs. Users can link information to ARIN so that everyone can find their repository and its contents. This model is ideal for larger organizations that need to delegate RPKI to their customers or other business units.
- Hybrid RPKI is for those who want to control the generation of their own certificates and rely on their RIR for publication. The user generates certificates, and ARIN does the publication. Plus, users do not need to manage the repository.
Curran then discussed RPKI for legacy blocks and the RPKI Relying Party Agreement (RPA).
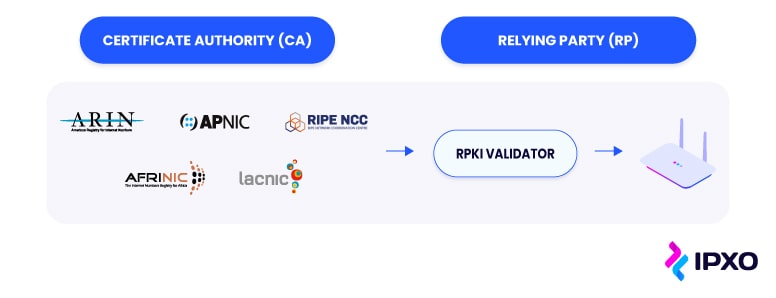
What are the obstacles organizations face while managing networks?
Aelmans suggested that, technically, RPKI is in place for networking vendors, as it is quite straightforward to configure a validator and start validating routes.
However, some issues with RPKI deployment can come up. According to Aelmans, it might be challenging for some network engineers to reject invalid routes. That is because they believe that the more routes one has, the better connectivity would be.
“On one hand, technically, it is relatively straightforward to configure a validator, set up a connection from your router and build policy. The rest, around it, still requires the majority of work.”
Trenaman shared some statistics on the RPKI adoption and added that in the RIPE region, 52% of routes originated in the region have ROAs. However, the number of RPKI BGP announcements that are invalid for IPv4 is very low. On the flip side, “2.5% of the IPv6 prefixes that have a ROA do not match what we see in BGP.”
According to Trenaman, this percentage shows that when people create ROA in IPv6 and make a mistake, nobody alerts them. Trenaman pointed out that people tend to forget to add IPv6 in their alerting and monitoring systems. She concluded that we should pay attention to ROAs in IPv6 as well.
What are the obstacles to moving millions of IPs every day using RPKI?
Anfalovas dove into the topic by sharing his thoughts on the delegated RPKI model. He claimed that, by default, the delegated RPKI assigns all the organization’s resources, more specifically, control of RPKI resources, to a specific certificate authority.
However, sometimes you might want only to subdelegate a specific part, for example, subnets. Delegated and hybrid RPKI methods allow internet users to specify the ranges that need to be subdelegated.
Unfortunately, it is risky to fully automate RPKI delegation when using a hosted RPKI solution. For example, ARIN’s RPKI is not fully automated, which means that technical personnel review information manually. This creates a risk of potentially losing RPKI information.
Anfalovas shared his belief that it would be best for hosted RPKI to offer this functionality. “You can currently subdelegate the control of Whois data for specific ranges, and you could also subdelegate the control of RPKI as well. That would mean that no more CAs would be needed and, basically, everything would be controlled on the RIR side.”
Vincentas Grinius added that subdelegation might be difficult for large enterprises because they must go through security audits, open new ports and make other arrangements with the relevant RIR.
What are the plans to offer RPKI flexibility?
Curran responded to the thoughts expressed by Anfalovas and Grinius by sharing that when ARIN first introduced the hosted RPKI offer, the RIR’s concern was whether or not its engineering and registration teams could successfully create an ROA for a network on behalf of organizations.
Curran agreed that ARIN cannot set up ROA on a user’s behalf, and many users complain about the complexity of the hosted RPKI system. In response, ARIN is now looking for ways to allow users to log in and “delegate parts of their authority on their accounts to other organizations.” Curran concluded that there will be more services that the RIR can provide and finetune in the future.
Grinius suggested that the internet registries could work together to standardize RPKI, Whois and other services to make everything more straightforward. Curran agreed that people want real-time RPKI interfaces and a common standard that would make RPKI management easier and suggested that RIRs are likely to start offering more uniform services.
What are the current obstacles adopting RPKI? What could make RPKI adoption faster?
Trenaman suggested that RIRs must do more in terms of RPKI deployment. As security is becoming increasingly important, RIRs must put a lot of effort into information security and resilience.
RIPE’s Routing Security Programme Manager also added that RIPE aims to perform 24/7 routing operations that bring the rock-solid infrastructure and more transparency to their services. At the end of the day, all RIRs ask their members for feedback on how they can improve.
Trenaman emphasized that, overall, RIPE sees a significant uptake in RPKI. For example, big transit providers are making route origin validations and routing decisions. However, large internet service providers (ISPs), for example, do not yet deploy RPKI in large.
Finally, Trenaman concluded her insights with some statistics. 75% of RIPE members created certificates in their dashboard, but only 58% created ROAs. What does this mean? It is crucial to educate people more about the importance of RPKI and how to create routing statements.
Would RPKI adoption on all networks eliminate the IP hijacking problem?
Curran quickly pointed out that if you have RPKI, the odds of route hijacking or typing mistakes, are greatly reduced. However, it is not possible to avoid accidents completely. Common route hijacks may be avoided entirely, but more technically sophisticated attacks can still occur. Nonetheless, Curran hopes we will have fewer serious attacks with the help of RPKI.
What does the IETF do to make RPKI more sustainable?
Aelmans introduced the main IETF function: To standardize how internet protocols work. He emphasized that IETF defines standards, but the user is responsible for implementing them.
Aelmans pointed out that the Secure Inter-Domain Routing (SIDR) Working Group is crucial in making different documents related to RPKI. For example, this Working Group develops guidelines on how to deploy and operate different technologies. These include RPKI, Origin Validation of BGP announcements and Border Gateway Protocol Security (BGPsec).
He added that, unfortunately, BGPsec is hard to deploy and is not widely adopted. For one, it poses control challenges because BGPsec requires more resources to handle it. The panelist also pointed out that BGPsec exposes security issues. For example, BGPsec does not check what origin was originally advertised. Aelmans concluded that BGPsec and AS path validation deployed together with origin validation might be a solid solution for BGP hijacks.
Don’t miss out on other great insights
The panelists concluded the discussion by sharing their thoughts on whether or not RPKI can become a self-sustained vehicle. If you want to hear the full discussion, watch the recording of the webinar below.
Interested in joining our webinars live? Follow our LinkedIn channel for updates about upcoming events, and subscribe to our YouTube channel to access all recordings.
About the author
Table of contents
What is RPKI, and why is RPKI important?
How RPKI emerged
How does RPKI solve problems from a network standpoint?
What is the ideal scale of RPKI adoption?
What are the key aspects of Hosted, Delegated and Hybrid RPKI?
What are the obstacles organizations face while managing networks?
What are the obstacles to moving millions of IPs every day using RPKI?
What are the plans to offer RPKI flexibility?
What are the current obstacles adopting RPKI? What could make RPKI adoption faster?
Would RPKI adoption on all networks eliminate the IP hijacking problem?
What does the IETF do to make RPKI more sustainable?
Don’t miss out on other great insights
Related reading

The Do’s and Don’ts of IP Address Abuse Observability
As the IPXO Abuse Prevention team continues to improve services and ensure high abuse observability at the Marketplace, let's take a look at the do's and don'ts that every…
Read more
Infographic: IPXO 2022 Q3 Abuse Prevention Statistics
Your comprehensive view of the IP address abuse handling at the IPXO Marketplace during the third quarter of 2022.
Read more
Infographic: IPXO Q2 2022 Abuse Prevention Statistics
A comprehensive view of the most common threats IPXO Abuse Prevention experts faced during the second quarter of 2022.
Read moreSubscribe to the IPXO email and don’t miss any news!
