What Is IP Spoofing, and How To Protect Yourself Against It
7 min read
15 October 2021
Vaidotas Januška
Learn more about IP spoofing and how to prevent IP spoofing attacks.

About the author
As a Chief Technology Officer at IPXO, Vaidotas is responsible for platform management and product development with engineering culture at heart. His greatest interests lie in cloud-native applications, technology trends, change management and organizational culture, coaching and mentoring. Vaidotas’ free time is occupied by sci-fi movies, nature and crafting things.
Table of contents
Related reading

13 October 2022 •
Internet Protocol,
IPv4 for Business
Dedicated IP vs. Shared IP Addresses for Email Marketing
What are the roles of dedicated and shared IPs in email marketing? Which option offers more benefits for businesses? We have the answers for you.
Read more
15 September 2022 •
Internet Protocol,
IP Reputation
IP Warming for Email Campaigns: What Is It and Why Is It Important?
What is IP address warming? How does it work? What kinds of challenges can you face when warming IPs? How can you benefit from this practice? We've got all…
Read more
2 August 2022 •
Internet Protocol,
Networking Protocols
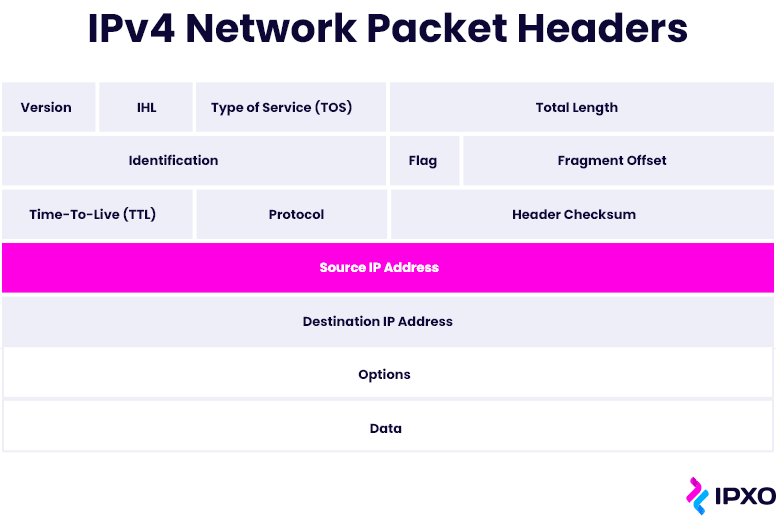
IPv4 Packet Header: Format and Structure
When you think about it, the IPv4 packet format is truly fascinating. Learn about the elements at play with this comprehensive guide.
Read moreSubscribe to the IPXO email and don’t miss any news!